🔹 2007 – The Birth of Mimikatz
Benjamin Delpy, a French security researcher, created Mimikatz as a proof-of-concept tool to demonstrate vulnerabilities in Microsoft’s Windows authentication protocols, specifically around credential storage and memory handling.
🔹 2011 – Public Release on GitHub
Mimikatz becomes open-source and available on GitHub. This gave ethical hackers and malicious actors alike direct access to powerful credential dumping tools like sekurlsa::logonpasswords and Kerberos ticket manipulation.
🔹 2012–2015 – Weaponization Begins
Advanced Persistent Threat (APT) groups start incorporating Mimikatz into post-exploitation frameworks. Major nation-state cyberattacks like APT28 (Fancy Bear) and APT29 (Cozy Bear) use it in high-profile operations.
🔹 2017 – WannaCry & NotPetya Leverage Mimikatz
The infamous ransomware attacks WannaCry and NotPetya included Mimikatz in their toolkits to spread laterally via pass-the-hash and pass-the-ticket exploits across enterprise networks.
🔹 2020 – Mimikatz Defenses Improve
Microsoft and major security vendors start implementing LSA protections, credential guard, and event logging to detect Mimikatz-like behavior. However, attackers evolve with fileless attacks and PowerShell variants.
🔹 2023–2025 – Mimikatz Remains Relevant
Despite newer tools, Mimikatz remains a go-to for red teamers and attackers alike. Regular updates from Delpy keep it compatible with Windows 10 and 11, and newer attacks such as Kerberoasting and Overpass-the-Hash are improved.
🔍 Why Mimikatz Still Matters in 2025
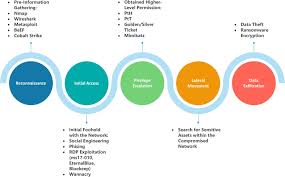
Whether you’re a cybersecurity analyst, pen tester, or IT administrator, understanding Mimikatz’s evolution helps you predict modern attack methods. Defending against Mimikatz means enforcing strict admin control, disabling credential caching, and configuring LSA protections — all vital parts of securing a Windows network.
Let me know if you’d like a visual infographic version of this timeline or a longer 2,000-word guide